Develop Your Housing Organization's Cyber Incident Response Plan [Playbook]

Despite a housing organization’s best efforts to boost cybersecurity, not all incidents can be prevented. To prepare for and respond to these breakthrough attacks, organizations should develop a cyber incident response plan outlining steps to minimize losses, fix weaknesses, and restore services.
At a high level, this might not sound dissimilar to a business continuity plan. Your cyber incident response plan and business continuity process should be in sync. Responding to a cyberattack is a “complex undertaking” that requires “substantial planning and resources,” according to the National Institute of Standards and Technology (NIST) Computer Security Incident Handling Guide.
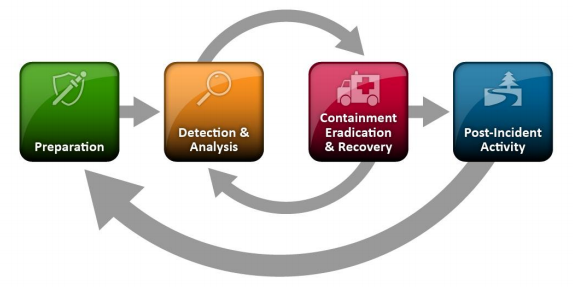
The NIST guide lays out a four-phase approach for handling cybersecurity incidents:
-
Preparation
-
Detection and analysis
-
Containment, eradication, and recovery
-
Post-incident activity
Richard Moore, CEO of cybersecurity firm CyberSix, explains how housing professionals should approach each phase in developing their cyber incident response plan.
“Having a plan is one of the first steps in addressing cybersecurity, and it costs only time and effort,” Moore said.
Preparation
During the preparation phase, develop a policy that defines what your organization considers a cybersecurity incident. Include any internal and external reporting requirements, including your insurance carrier’s claim filing details. This policy should be used to inform the details of your cyber incident response plan, including the structure of your cyber incident response team and how often the group meets.
If possible, the plan should include different “playbooks” for different types of cybersecurity incidents.
“You should create playbooks for different cyber threats and one executive playbook to allow for smoother and less stressful approaches to incidents,” Moore said.
Your incident response team should include employees or vendors with technical, legal, human resources, and communications expertise. Management should be represented, as should an employee from the department that was compromised.
Cyber incident response team members can be part- or full-time depending on the size of your organization and the frequency of cybersecurity incidents. You can also rotate members in and out of your incident response team and allow members to perform other tasks.
“Incident response teams should meet semi-annually at a minimum if no actual incidents have occurred to walk through and test out the playbooks,” Moore said.
Prepare to prevent
A crucial part of the preparation process is ensuring mitigation efforts are in place to prevent successful cyberattacks in the first place. Moore suggests employee training through an in-house subject matter expert or your cybersecurity training vendor.
“Having a subject matter expert or platform that can support education is what all companies should be doing to educate their employees,” he said.
Your in-house IT team or consultant should also:
-
conduct periodic risk assessments of your system;
-
patch your system whenever software updates become available;
-
maintain network security and monitoring; and
-
provide quarterly reports on the status of threats and security updates.
Moore suggests moving any on-premise equipment such as servers to a cloud computing service
like Azure or AWS, because if your organization has limited in-house expertise, “no one is really taking care of your physical equipment, including updates and security.”
Multifactor authentication (MFA), also called two-factor authentication (2FA), is a must-have for housing organizations because it adds a layer of protection that makes it more difficult for cybercriminals to access your systems.
“MFA is a security enhancement that requires you to present two pieces of evidence—your credentials—when logging into an account,” Moore said. “You probably used MFA in some form already: at the ATM, for example, when you put your bank card into the machine and it asks for your PIN.”
Your credentials can fall into any of three categories:
-
Something you know (e.g., password or PIN)
-
Something you have (e.g., mobile phone)
-
Something you are (e.g., fingerprint)
To enhance security, your credentials must come from two different categories.
“Entering two different passwords would not be considered multifactor,” Moore said.
Investigatory resources
Consider having a cyber forensics firm on retainer. Most organizations don’t have the resources or expertise to diagnose a cybersecurity threat alone.
A forensics firm’s primary objectives are to:
-
investigate the source of the breach and contain potential threats;
-
identify the extent of sensitive data accessed by cybercriminals; and
-
fix vulnerabilities to prevent a similar breach from happening again.
External legal counsel should also develop a detailed timeline of events and communications, including crucial forensics details.
Consult with your internal legal counsel before entering into any agreement with an external service.
Media relations
Be prepared to handle media inquiries about any potential cybersecurity incident. Your cyber incident response plan should include procedures that comply with your organization’s media interaction and information disclosure policies.

For example, many organizations find it helpful to designate a single point of contact and at least one backup. Consider conducting media training sessions for your entire incident response team that include mock interviews and press conferences.
During a cybersecurity breach, your incident response team should also maintain an incident narrative, preferably with oversight from external counsel to ensure any sensitive internal communications are shielded by privilege.
At a high level, the narrative should describe the initial point of entry, breach tactics, and crucial instances of data compromise. This narrative is a starting point for all external communications, including media, to ensure consistent and accurate messaging.
Detection and analysis
There’s no shortage of cyberattack vectors that can affect your organization. Ransomware is a common attack, particularly in the housing industry, due to the personally identifiable information (PII) you collect and store. Determining if and how an attack occurred is often the most challenging part of the incident response process.
As noted in the previous section, your in-house IT team or consultant should monitor your network for signs of a breach. Employees trained in identifying common attack methods (e.g., social engineering tactics like phishing) should also report any unusual activity outlined by your cybersecurity policy.
If you identify a potential threat early enough, your organization may have an opportunity to avoid a breach by updating network settings/software, warning staff, and monitoring the situation closely.
If all signs point to a potential breach, your organization should contact a cyber forensics firm (ideally, this firm is already on retainer) to investigate. Your cyber incident response team should also notify internal and external stakeholders designated by your cyber incident response policy.
Law enforcement coordination
After a breach, notify law enforcement if it aligns with your organization’s cybersecurity stance, Moore noted.
“When sharing information with law enforcement, I would recommend sending only the information necessary to conduct a criminal investigation,” he said. “This should align with the organization’s position on ‘pursue and prosecute’ or ‘defend and contain.’”
Most law enforcement agencies that deal with cybercrime have anonymous submission platforms to share sensitive information without any repercussion to the organization. The NIST Computer Security Incident Handling Guide recommends contacting only a single law enforcement agency to avoid jurisdictional conflict.
Containment, eradication, and recovery
In this stage, your cyber forensics firm should work closely with your cyber incident response team to develop a containment strategy before an incident overwhelms resources or increases damage.
For example, NIST lists “sandboxing” as a form of containment in which cybersecurity experts monitor the attacker’s activity in a contained environment to gather additional evidence. Before implementing a containment strategy, discuss the pros and cons with your organization’s legal counsel and cyber incident response team.
Your forensics firm should also gather evidence, if possible, to help resolve the incident and assist with any potential legal proceedings. If necessary, the firm may eradicate components affected by the incident, such as breached user accounts.
Once your forensics firm remediates any outstanding threats, your IT team can restore your system to normal operations. In some cases, your organization may need to restore the system from a backup or rebuild it from scratch, which can be costly.
Post-incident activity
After the immediate threat is neutralized, housing organizations should perform “a postmortem analysis of what and who is impacted by the breach,” Moore said.
Learning and improving
Your organization’s postmortem analysis should also focus on learning and improving.

“Ensure that you have followed your playbooks, updated them based on any changes, and communicated clearly and with facts about what happened and how the organization responded,” Moore said. “This is a defensive move to protect your reputation.” Your organization should also ensure all processes are understood and well documented.
“For example, if you have a process for transactions and payments, you should never fall for the CEO sending you an email to transfer funds,” Moore said. “That should alert you that someone is trying to surveil your environment.”
Work with your IT team and forensic firm to repair gaps and vulnerabilities as soon as possible.
“The biggest mistake I see organizations making after the attack is actually doing nothing and thinking that the containment was all that was needed,” Moore said.
Reporting
It’s essential that your forensics firm attempt to determine whether cybercriminals accessed any personally identifiable information (PII), and if so, whom the organization may need to notify based on state regulations.
Every state has a law requiring notification of security breaches involving PII, such as Social Security numbers (refer to your state-specific breach notification law for details).
Notify your insurance carrier(s) and prepare to file claim information within the contractually required timeline. This should be a formal notification, by either ticket system or email, with the email added to the meeting minutes for your board of directors.
Moore noted that it takes most organizations about six months or longer to fully recover from a significant data breach.
“A formal written report should always be issued at the end of the investigation that concludes legally what happened and what the facts were,” he said. “These reports should be non-opinionated and simply stated. Executive management and your legal counsel can determine what should be included in the overall final report, but facts are important to have while building a remediation plan.”
Contact our Risk Control and Consulting team for more resources and answers to your housing organization’s risk-related questions.
Interested in working with HAI Group? Our Account Services team is ready to assist you.

Includes copyrighted material from a company under the HAI Group family, with its permission. This post is for informational purposes only and is not intended to provide legal advice, and shall not be relied on as such. We strongly recommend consulting with legal counsel or an appropriate subject matter expert.